How commercial SATCOM can prepare for defence missions - Defence Industry Europe
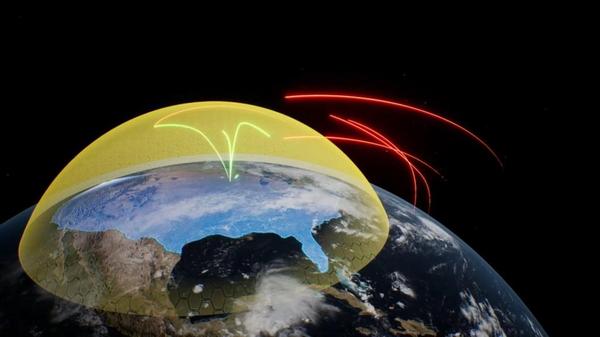
By Mike Adamson, BGen (Ret’d)From ports to tanks to airplanes, militaries have historically owned and operated the means and infrastructure by which they conduct missions. For modern militaries, satellite communication (SATCOM) networks are a critical part of that infrastructure. That said, very few defence organizations have the significant resources to launch, operate, and maintain their own proliferated constellations of tens, hundreds, or even thousands of satellites; even as the need for sa...
 Filters & Sorting
Filters & Sorting